X509 Certificates vs. API Keys in RavenDB
RavenDB 4.x is using X509 Certificates for authentication. We got a feedback question from a customer about that, they much rather to use API Keys, instead.
We actually considered this as part of the design process for 4.x and we concluded that we can make this work in just the same manner as API Keys. Here is how you can make it work.
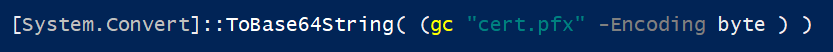
You have the certificate file (usually PFX) and convert that to a Base64 string, like so:
[System.Convert]::ToBase64String( (gc "cert.pfx" -Encoding byte ) )
You can take the resulting string and store it like an API key, because that is effectively how it is treated. In your application startup, you can use:
And this is it. For all intents and purposes, you can now use the certificate as an API key.





Comments
If only it were that simple... I love the idea of using client-certs. In theory. In practice X.509 is a hot mess of more or less broken/non-compliant/standard-interpreted-in-a-slightly-different-way kind of implementations as well as a ton of user confusion (which PKCS#x is my file here? what parts of it have encryption at rest applied? which password for what etc.)
We tried using client certs from the bundles generated by RavenDB Server 4.1.5-patch-41012 and had the following problems:
In the end, we didn't have the time to properly trace this down though we saw some work being done in that area on RavenDB's that sounded scary enough not to dig in deeper https://github.com/ravendb/ravendb-jvm-client/commit/2631abf0acb8e10fd3c89281930d3cba67b6e7a7 At that point we already spent almost half a day of engineering time on this.
The only workaround that did the trick for us was to generate the cert with a password in RavenDB Server and the "roundtrip" the cert through openssl, stripping the password in the process. The "passwordless" files from RavenDB server didn't work (either with null or "" password when trying to load into a KeyStore). It appears the roundtrip through openssl fixes something important that makes the pfx file more amenable to a JVM running on linux...
~~~
enter "password" on all prompts
openssl pkcs12 -in rvn0.pfx -out rvn0.1.pfx
enter "password" on all prompts, EXCEPT when asking for "Export Password"
openssl pkcs12 -export -in rvn0.1.pfx -out rvn0.2.pfx
When imporing to Chrome or Firefox, leave password empty when prompted
```
Johannes , I found that
PFXfiles work great on Windows, but on Linux, it seems thatPEMfiles are have far better support.If you can send us reproduction steps, we can look into that.
Comment preview